The architect of a major scam operation, Bryan Seely tried to make amends. As a whistleblower, he created a hack designed to get top level attention. As soon it went live, Seely realized he was in over his head. He had wiretapped two major federal agencies. With each new call recorded, the illegality only got deeper.
1. A talk in Tokyo
In the skyline bar of Tokyo’s Prince Park Tower, Rick Seely is winding down the day with a beer and some conversation. A longtime American expat nearing retirement age, Seely looks out at the megacity at dusk, the lights of nearby skyscrapers flickering on, Japan’s Eiffel Tower replica glowing orange. The topic at hand is Rick’s son Bryan, a young ex-Marine and increasingly well-known hacker in Seattle.
Rick is discussing the chances that his son will be murdered.
“I always thought he’ll just disappear one day,” Rick says, sipping his Asahi lager. “Bryan will get the wrong people angry, and that’ll be it.” He stares out the windows, his expression not so much forlorn as accepting of a tough truth. “We’d never hear from him again. He’d be ‘disappeared’ by someone.”
With a big mustache and warm intelligence, Rick seems every bit the good dad. His concern is mixed with a deferential attitude, letting his boy make his own mistakes. This is the first time he’s discussed Bryan with someone outside the family, he says. There are things he needs to get off his chest.
He can’t understand why Bryan commits federal crimes, the type that gets people put away for life. Why he willfully pisses off criminal enterprises and massive scam networks, one of which used to employ him. Bryan has an ex-wife, three kids and pays the bills through IT contracts. Why is he pulling the tails of tigers?
Rick and Bryan had a frigid relationship for many years, but it’s thawing. They talk more now, but the son’s motives nonetheless remain a mystery to his father. Bryan’s former attorney, Bellevue-based Brian Muchinsky — who says the federal government would have Bryan “dead to rights” on a few serious crimes – will later tell me his client is simply a honorable guy out to expose wrongdoing. Muchinsky still later will revise his opinion, saying Bryan scammed him out of money.
Months after my discussion with Rick, I’d be back in Seattle, talking to Bryan and presenting his father’s assessments and predictions for a possible “disappearance.” He’ll laugh, praising his father’s smarts and playing the “I’m just doing the right thing” card. But after a few beers and some persistent questions, Bryan reflects more deeply, and his motivations become clearer. To him, the work is some form of self-redemption, and some form of revenge.

2. Anatomy of a scam
The work of hackers can seem like a rare thing to most people, with little effect on their day-to-day. Armies of coders, largely in Eastern Europe, hijack credit cards, bank accounts, and entire computer networks. Governments steal secrets from enemies and allies. The user database of the adultery-enabling service Ashley Madison gets aired out by those with a point to make.
But there are other forms of hacking that inflict damage on thousands of small businesses every day around the world. Bryan Seely would know. Between 2008 and 2010, he worked on this side of things, conducting what is known as “map spamming.” He says the recession drove him to it, eliminating his IT position at a law firm and leading him to become the technical architect of a multi-million dollar scam operation. And for his attempts to make amends, he could get thrown in prison, or possibly worse.
To illustrate the scam, let’s say you’re a locksmith with a shop on the outskirts of a big city. If customers in the city Googled a locksmith service, yours wouldn’t be among the top results. Using a few relatively simple tricks, however, you fabricate some listings on Google, Yelp, Yellowpages.com, and more. You create fake businesses with specific addresses all over the city in question, and new phone numbers that forward to your own. It doesn’t matter that there’s no storefront at these locations — locksmiths do most of their business remotely. Business owners can do this themselves with some light self-training, or hire someone like Seely.
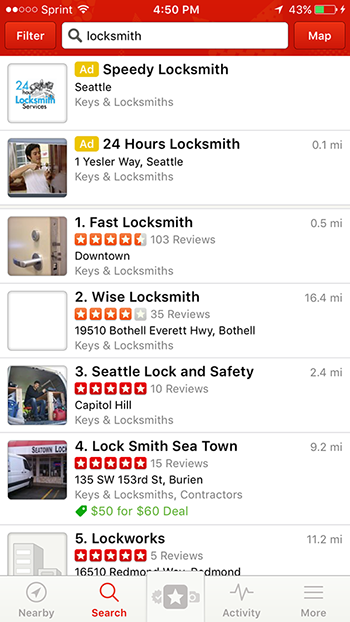
Eventually, the calls pour in and you need help answering them all. You hire some receptionists, maybe even set up a call center. You don’t have enough locksmiths to handle all the business, so you start selling leads to nearby competitors. If you’re ambitious, you buy some ads and hire someone to game the online search results further, making your competitors less prominent through spammy bad reviews, flags and other tricks, and bumping up your own listings. If you’re especially ambitious, you start listing locations outside the city, region and even state. There’s no real limits.
“By the time I stopped in 2010, we had 3,126 fake businesses listed around the country,” Seely says.
He is describing his part in a scam — based in Southern California and run by a man he simply refers to as “Rob” — that he says remains in operation today, bringing in $10 million annually by Seely’s estimation. As evidence, he presents Excel spreadsheets of still-listed fake phone numbers, as well as thousands of fake online reviews that can be found in identical form on Yelp listings across the country. Over the course of an hour, demonstrating fake listings and showing how they’re created, he backs up his claims with a great deal of thoroughness.
Seely’s scam listings weren’t for locksmiths, but auto glass repair. No matter. Any business that offers a remote service — landscaping, garage door repair, locksmithing and so on — is fair game, he says. It’s not a technically advanced hack, but it’s lucrative.
According to the Washington Department of Licensing, there are three licensed businesses in Seattle with “locksmith” in their business or trade name. The top result on Google and Yelp, Fast Locksmith, is not one of them. A search for “locksmith” on Yellowpages.com yields 4,005 results in the city, with nearly 100 new additions since this past summer.
Approaching licensed businesses like Broadway Locksmith about the issue, the owners and staff respond eagerly, with variations of “How long have you got to talk about this?” Many, including Seely, suggest some of the scam’s biggest operators are likely based out of Israel.
“These scammers are so organized,” says Broadway Locksmith’s Bjorn Madsen. “They call us all the time, offering $20 leads. They have national phone banks and call centers. They pay Google and Yelp and buy out all their ad results. It’s a big, big problem for honest, licensed businesses.”
Citing a growing disgust with himself, Seely quit scamming in 2010, and carved out a traditional IT career in Seattle. Three years later, seemingly on a lark, he decided to check on the state of map spamming in the United States. Rather than seeing an improvement in security by Google and others, he realized things had gotten much worse.
In reaction, Seely became the epitome of a failed whistleblower. From late 2013 to early 2014, he harped at Google about the sort of issues he used to exploit, going so far as to reach out to individual project managers and engineers. No one at the company took him seriously, he says, rejecting his work as trivial. Journalists and law enforcement agents met the issue with a similar indifference. So, in a bid for attention, he resorted to drastic measures.

Seely takes a selfie before confessing his crimes to the Seattle field office of the U.S. Secret Service.
3. Hitting the Feds
Creating fake listings is not the only thing semi-skilled hackers can do on Google. They can also manipulate existing listings. They can change the hours of a business, for example, or even its phone number and address. In a Wired magazine article last year that cited Seely’s work, business owners said these activities can bury them.
Fake listings on Google are particularly pernicious, because the service operates as a trusted phone directory for people around the world. Seely says Google is extremely slow to respond to complaints by businesses whose listings have been manipulated. But when a company or restaurant is incorrectly listed as closed on weekends, that can mean serious lost revenue.
To draw attention to the issue, in February 2014 Seely created two phone accounts, which he then attached to the Secret Service headquarters in Washington D.C. and the FBI office in San Francisco. By manipulating search results, the new numbers became the default contact for these two offices. He set the numbers up to forward calls to the actual agencies, only with the conversations now being recorded through an automated online system.
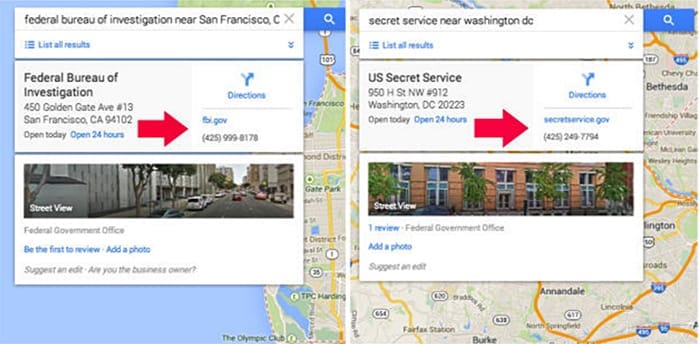
“I could’ve done this for every congressman, the White House, mayors, lawyers, banks, foreign embassies, you name it,” Seely says. “I could’ve recorded everything, and no one would’ve noticed for a long time, because the phone number I set up just forwards to the original. So everyone’s getting to the right destination. No one would think anything went wrong.”
The moment the hack went live, Seely realized he was in over his head. He had wiretapped two major federal agencies. With each new call recorded, the illegality only got deeper. He contacted some former Marine buddies for advice, and they all essentially said, “Turn yourself in immediately.” It was his only hope for avoiding jail time.
Walking into the Secret Service office in downtown Seattle and informing agents there of his crime, he got roughly the same reaction he received from Google — a “stop wasting our time” attitude. Seely still fumes at the memory.
“For me to pull this off and them to roll their eyes, I just had to say, ‘Screw you. Pick up your phone and call your D.C. office right now,’” Seely says.
An agent did so, using the default number that came up in a Google search. Immediately after the agent’s call ended, Seely received a text on his phone, informing him of a new recording. He played both sides of the phone conversation back to the agents. “It was like magic. The look on their faces was like, ‘Oh, shit. Kill it with fire. We need to kill this immediately.’”
The Secret Service read Seely his rights and locked him in an interrogation room for a while. They did not jail him, but left the door open to doing so in the future. He says they simply demanded he cease his campaign immediately.
“And when the Secret Service tells you to stop something or else,” Seely says, “you stop.”

4. The promotional trail
Seely never really stopped, though. The wiretapping ended, but he has continued poking at both the federal government and scammers. He provided his recordings of FBI and Secret Service calls to online news organization Gawker, and spoke to Seattle’s KOMO News about his accomplishment.
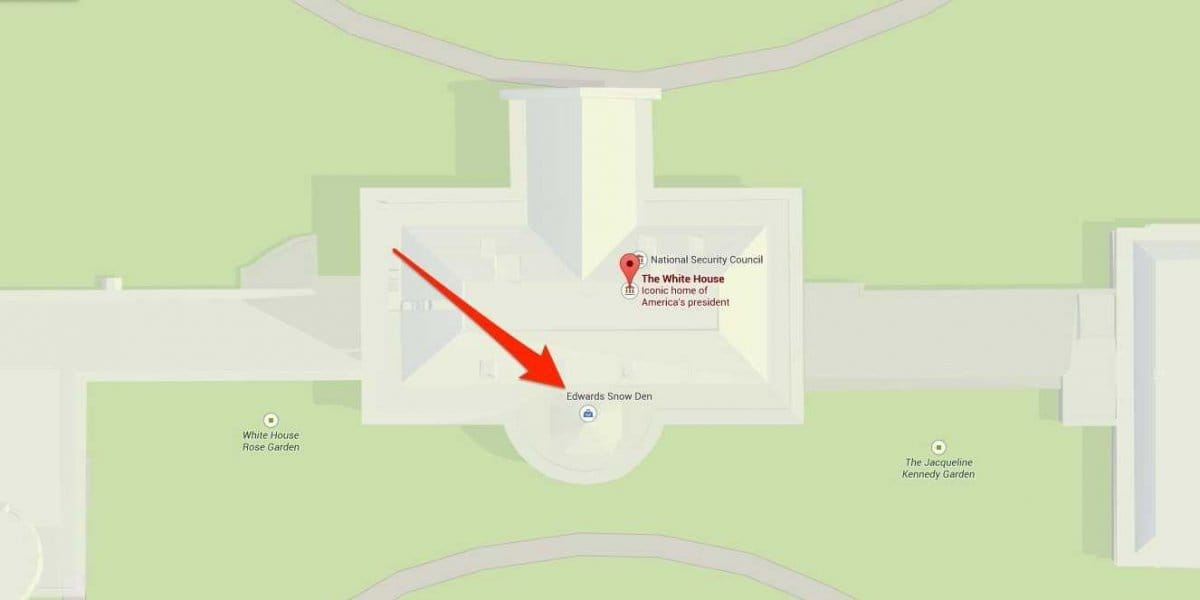
Earlier this year, he created a verified business listing for “Edward’s Snow Den,” made to appear on Google Maps as if it were situated within the White House. At a local TEDx conference he delivered a speech titled, “Wiretapping the Secret Service Can Be Easy and Fun.”
This was followed in July by the self-publication of “Cyber Fraud: The Web of Lies”, a book he co-wrote with Muchinsky, his former attorney. A copy he provided to me lays out in explicit detail how search engine scams operate.
There is a certain braggadocio common to hacker circles, a narrow megalomania. For many hackers, there’s nothing better than proving themselves smarter than a system. They often can’t help but let others know about it. The difference is most hackers do this behind a veil of attempted anonymity. Seely is zealous about putting his name and face out there, perceiving this self-publicity as necessary for his whistleblowing to have any effect.
But this approach has led to emailed death threats, says Seely, from people who don’t want their scam operations publicized. He showed me one example of an anonymously sent text: “When we find you, you are finished.” Upon the announcement of his book, both he and Muchinsky say the Secret Service has taken a renewed interest in his case, and not in a good way. Muchinsky says the agency could “bring the pain” legally if they don’t like what they read in it.

Seely later took the book off of Amazon, saying he’d spoken with federal agents, and was left with the impression that he either “edit the book or spend a long time in prison.”
To hear both he and Muchinsky tell it, the feds are saying he’s had his fun and made his point, and it’s time to shut up already.
Seely says his work has caused Google to disable some, though not all, of the easiest exploitable flaws in its system. But given the fact that he’s the father of three, one a newborn, it might be difficult to understand what’s going through his head as he continues to pursue the issue.

5. The enemy
Back in Japan, Rick Seely praises Bryan’s ex-wife for providing a steady home for the kids while his son tilts at windmills. For the life of him, he can’t see Bryan’s continued campaign as anything but irresponsible.
Presented this assessment, Bryan says it’s hard to understand the way his scamming work affected him.
He started doing it out of financial desperation, he says, not quite knowing what he was getting into. This he blames partially on “Rob,” the head of his former auto glass operation, who hired Seely for his technical expertise. When he describes seeing Rob — “one of the worst human beings on earth” — living in an Orange County mansion, raking in millions that would otherwise go to legitimate small businesses, he simmers and curses. It’s an ongoing injustice, subtly nagging at him like a splinter. He wants to wipe it out.
But in the end, it’s not Rob’s fault that Seely gamed the system for more than two years. He knew what he was doing. No matter how irrational some of this campaign may seem — “I’ve never said I was smart,” he says — it’s something he believes must continue if he’s to look at himself in the mirror.
“I was the bad guy for a while,” Seely says. “I really was, and I can’t forget that. We weren’t physically hurting people, but we were hurting them in other ways. I might’ve caused the breakup of families because a guy was so stressed from losing his business that he got divorced. Kids might be leading much worse lives because of what we did. This is all I know to do to make up for my mistakes.”
When I return to Seattle from Tokyo, an odd note awaits in my mailbox. It promotes a locksmith with the same exact address as my apartment building. Previously, I would’ve been baffled by it, thrown it away, and not given it another thought. Instead, I call the business it lists, and ask multiple people where they’re actually located. An answer never comes.
There are thousands of underground businesses in every major city – existing in name and contact info only – invisible, numerous, and just an online search away. They’re often the ones we invite to our homes.
--
Drew Atkins is an editor and writer for Crosscut. For comments and tips, please contact editor@crosscut.com.
A version of this story originally appeared in Seattle Business Magazineand Seattle Magazine.
Photo credits, in order of appearance:
Seely profile: John Vicory
Tokyo Tower photo: Drew Atkins
Linux “shadow file”: Christiaan Colen
Seely presentation: TEDxKirkland
Google Maps and CNBC screenshots: Bryan Seely
“Everybody needs a hacker” photo: Alexandre Dulaunoy

